Walk-through 1 of 2
So to get started, I’d like to walk you through the lab environment a little. We begin with the basic Single Edge FortiGate firewall. This firewall offers both routing and stateful firewalling, as well as services such as Intrusion Prevention scanning, all inter-vlan routing both North-South and East-West, Web Filtering, DNS Filtering, and SSLVPN and IPsec VPN terminations to my other Partners in the Internet zone.
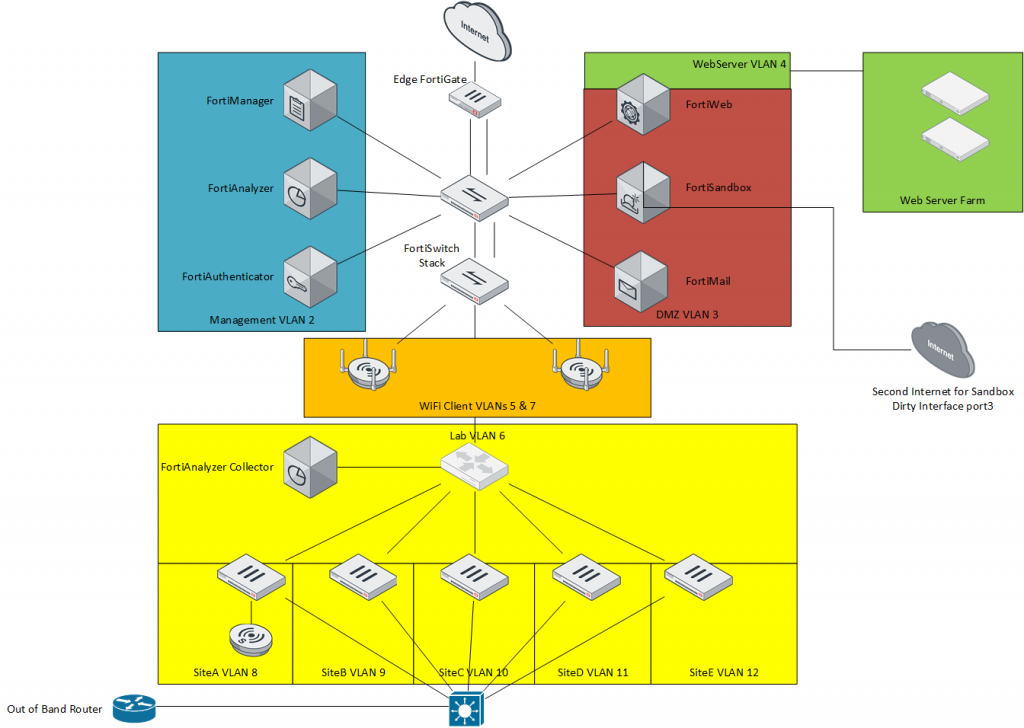
Attached to this FortiGate to expand it’s ports, and add PoE+ capabilities is a stack of FortiLink-managed FortiSwitches. The FortiSwitch is a welcome member of the Fortinet family of products and a logical extension to the FortiGate itself when managed by FortiLink. FortiLink is a proprietary suite of protocols used by Fortinet to provide Centralized Management of the VLANs, port configurations, trunking, firmware management, and when configured, MCLAG or LACP aggregation of links for improved inter-switch and Firewall-to-Switch communication. In my particular case, I have 1x FortiSwitch 108D-POE (10 port Gigabit switch with 4 PoE+ ports), a pair of FortiSwitch 248E-POE (48 port Gigabit switch with 24x PoE+ ports, and an additional 4 SFP 1 Gigabit up-link ports), and a single FortiSwitch 448D-FPOE (48 port PoE+ Gigabit switch with 4 SFP+ 10 gigabit up-link ports). I use the 10 gigabit ports with DAC cables to integrate with my VMware ESXi and HyperV hosts that house many of the Virtual Machines, which we will get into in a bit.
My lab and home WiFi networks are controlled by the built-in Wireless LAN Controller that’s included in the FortiGate firewall appliance. These have separate SSIDs, separate VLANs, and differing Policies within the Firewall to manage their access privileges, UTM/NGFW features, and Authentication settings. For instance, in a future article I will walk through changing the Lab WiFi network from Preshared Key authentication, to PKI-based 802.1x Authentication, and even loading 2 different subnets onto the Lab WiFi based on the profile of the User authenticated. You can use this in your environment, for splitting a company VLAN by User Login, to separate Sales from HR, for example.
Within the Management VLAN, I have a few key Fortinet components that very Security Fabric customer should have, or be considering to add very soon. The first is FortiAnalyzer. Then FortiAuthenticator. And for multi-site deployments, FortiManager.
FortiAnalyzer is Fortinet’s Logging, Monitoring and Reporting appliance. Contrary to popular belief, some people think that FortiGate is the only mandatory required device to have a “Security Fabric” – that is incorrect. The Security Fabric has 1 mandatory device, and that is FortiAnalyzer. “FAZ” as it’s known to those familiar with it and “FortiLingo” native speakers, is the appliance that collects logs from all your Forti”Things”, parses the logs, looks for Indicators of Compromise, Sends out Alerts, keeps track of your SOC Alerts, brings your NOC operations into the same tool, and produces scheduled and on-demand reports. The majority of my day when working with customers on troubleshooting problems, is spent in the FortiAnalyzer as it’s the Central Repository for all the logs, and offers great search capabilities across an entire company network worth of Security Appliances.
I’ll be doing a whole series just on FortiAnalyzer Logging and Reporting I’m sure.
For those of you that work at MSSPs or MSPs, FortiAnalyzer is the first tool I would buy to start an MSSP business – and yes, it can be to a degree, multi-tenanted. That is, everyone’s logs can be separated by Administrative Domains, and Admin User logins can be restricted to a single or any combination of ADOMs by the Super-Admin (you!). You can control what buckets of data a user can access, who can / can not run reports, Trusted Host IP addresses they can login from, Disk Space per ADOM is allocated and isn’t exceeded (so when CustomerA starts sending lots of logs, if they are allocated 50 GB of disk space, their logs start rolling at 50 GB without impacting CustomerB’s storage retention in their 50 GB of space). This allows you to set billing based on X-GB of storage, and enforce that automatically.
Next up is FortiManager, which is the Centralized Configuration Manager for the FortiGate, FortiSwitch, and FortiAP configurations. It does Centralized Management, a Single or Shared Policy Packages of Address Objects, IPv4 Firewall Policies, all the components required to make a Firewall Policy work, Audited reporting of changes, Change-Management procedure enforcement, as well as keeps historical versions of every configuration change made. This allows you to easily “roll back” a configuration change, schedule a change to occur in the future, and compare your live configuration to one in the past to see what has changed. Definitely a great tool if you have Auditors that want a report of Who/What/When/How changes to Policies were made (I’m looking at your, PCI-Compliance people!)
I then have in Lab VLAN 6 a collection of small FortiGates that I use to simulate branch offices / create IPsec Tunnel spokes / use for the example write-ups on this blog. Each has a VLAN behind them, treated as the “BranchX VLAN”. I also have a second FortiAnalyzer running on a VMware host in this network, in Collector Agent mode. Devices submit to this FortiAnalyzer, it collects and streams them back to the FortiAnalyzer Master Unit.
I’ll leave FortiAuthenticator and the DMZ devices to another post, as I’m sure most of you are glassy-eyed at this point.