Walk-thru 2 of 2
In my previous post “Lab Environment Design 1 of 2”, I went over many of the components in my Lab Environment at a fairly high level. We went over FortiGate, FortiSwitch, FortiAP, FortiAnalyzer and FortiManager. I touched on some ideas for starting an MSSP business around FortiAnalyzer, and how we use it in our business at the Partner that I work for.
Let’s take another look at that horribly drawn Visio diagram that I whipped up really quick:
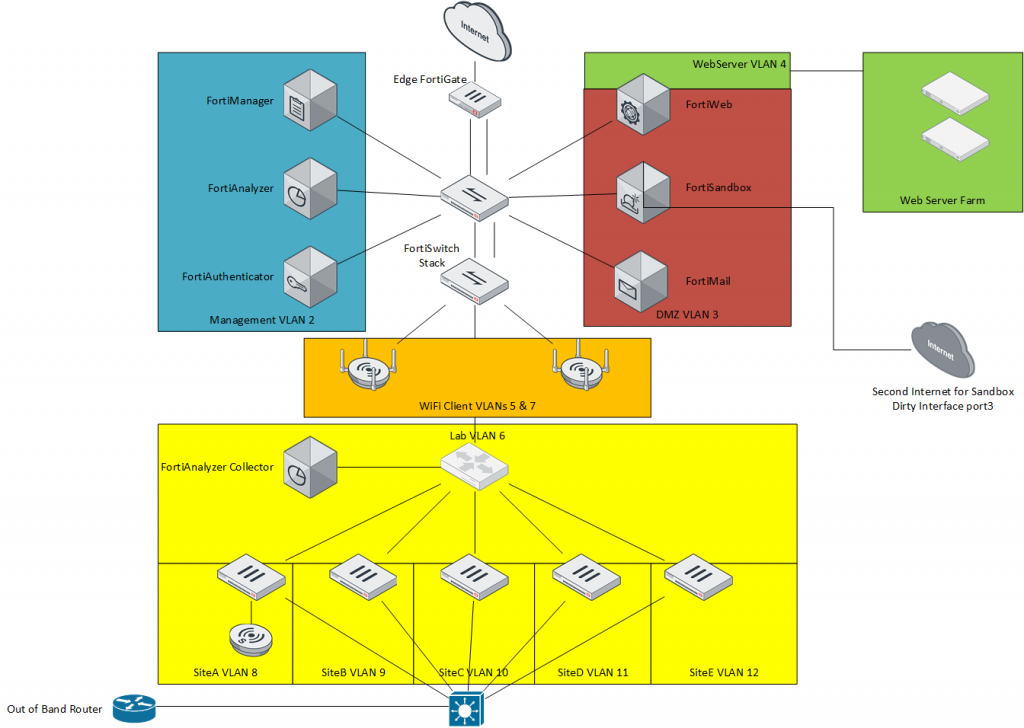
The components I haven’t really touched on of importance, are:
- FortiAuthenticator
- FortiSandbox
- FortiMail
- FortiWeb
And then I’ll just gloss over quickly, the Web Server Farm and Out of Band Router, and how they factor into the network design / test case scenarios here.
FortiAuthenticator
FortiAuthenticator (FAC for short in FortiLingo – everything has a Three-Level acronym mostly when talking internally at Fortinet and between Fortinet and Partners, to save having to say “Forti” 8000x a day), is the Identification and Authentication Manager for the entire Fortinet ecosystem and beyond. It can switch up RADIUS, TACACS, LDAP, Active Directory, SAML, Kerberos, Fortinet Single Sign-on, and 802.1x all 7-ways-to-Sunday. On top of it all, it’s a one-stop solution for RADIUS offering both a Certificate Authority to hand out and manage PKI Certificates, as well as 2-Factor Authentication using a centrally managed FortiToken repository for user login. In our lab environment, any of the internal CA certificates used only within the environment (for things like Deep Packet Inspection on the FortiGates to inspects HTTPS/SSH traffic with AV IPS and AppControl; to 802.1x Authentication) are all handed out and signed by FortiAuthenticator. My RADIUS authentication to my Active Directory using LDAP then authenticated 2nd-Factor with my FortiToken Mobile app on all my different FortiGates, is again handled by FortiAuthenticator.
There’s a long list of possible use-cases, included as an intermediary translator to integrate a bunch of third-party solutions into the environment. As is normal with standards-based protocols, it doesn’t just do it for FortiThings, either – I can do 802.1x Authentication for my HP Procurve switches, or TACACS+ authentication for login to my Cisco Out-of-Band Router as well.
FortiSandbox
This is a great tool! FortiSandbox is Fortinet’s Zero-Day Malware Detection device. When I download a file from the Internet, and my FortiGate does an AntiVirus scan of the file before passing it on to me – if the file is neither “Known Good” or “Known Bad/Malicious”, it will automatically submit the file to the Sandbox for analysis. Using heuristics, code analysis, Community Reporting (meaning it checks in with every single other FortiSandbox in the world before scanning the file and wasting resources), and finally actual “detonation” of the code by running it in a Windows Environment and monitoring it’s activity, the Sandbox determines malware that is so new that signatures don’t exist for it yet. It then reports back to the device that submitted the file, that it’s “Good” or “Bad”, and if “Bad” adds a signature to the AV Database locally, sends that to your FortiThings as an updated AV Database; and submits the hash of the file to the Community of all the other FortiSandboxes in the world, so that they can be protected from it as well.
The “Secondary Internet for Sandbox Dirty Interface port3” on the diagram is a representation that I actually have a separate IP address range from my ISP used by port3 on the FortiSandbox for it’s internet access. Remember, Sandbox lets the malware do all it’s nasty stuff (ransomware, submitting spam, downloading viruses, botnet Command&Control stuff) – a bunch of things that will get you put on blacklists – so I don’t want that messing up my Lab Environment. It does all this stuff using port3 on the Sandbox appliance. Away from my protected nework.
FortiWeb
Fortinet’s Web Application Firewall. Machine Learning-based algorithms, specific policies related to hosting Web Applications / Web Servers, protection from things like SQL Injection, scanning of uploads to web sites, and FTP Servers. Malformed web requests, logic-reasoning for eCommerce etc (ie, you can’t logically allow a user to load the Shipping page to send out the packing slip to ship their Cart of goods without going through the Payment Processing/Processed pages first).
FortiWeb has documents on doing Reverse-Proxy and Transparent protection of applications such as Microsoft Exchange Outlook Web App, fronting Front-End Servers, and in protecting and even offloading SSL Encryption from the backend server relieving Web Server resource requirements.
FortiWeb is great for putting in front of a small number of Web Servers as a miniature Application Delivery Controller / Load Balancer, as well. With health check, session persistence, and Reverse Proxy Rewrite, as well as modifying HTTP Header information; you can protect and host multiple servers to keep your web service online.
Web Server Farm
Well, this is generally pretty self-explanatory. A couple of Web Servers hosting different sites, some load-balanced between multiple Virtual Machines to show off the ADC/Load Balancing capabilities of FortiWeb. This website itself lives on a few Web Servers, with a syncronized SQL cluster for the Database.
FortiMail
My email for this website, trevor[at]securenet-central[dot]ca is hosted on a FortiMail VM which lives in my DMZ in my home lab. FortiMail is a great Email Security Gateway. You can front-end your Cloud Email, or Onsite Email Servers with it. At Secure Links, we use it to protect Customer Email Servers, whether they use Exchange On-Prem, Office365, G-Suite, or any other provider. Their email (MX Record) has “the Internet” send their email to our FortiMail, we scan and scrub and apply filters etc. in our FortiMail, and then send only the approved clean email to their actual Email Server (in the Cloud or On-Prem).
In my lab environment here, I actually use it in Server mode – so my email server is actually in my FortiMail VM. As I’m only a handful of accounts on this appliance, I’m served just fine at the moment. I will be looking to move another personal email’s email scanning to FortiMail infront of Office365 soon for that blog post.
In 2018, a study was done with FortiMail vs Exchange Online Protection, and showed that FortiMail caught more malicious and SPAM email, than Exchange Online Protection, with 0.00% false positives. This is partially due to FortiMail’s Integration with FortiSandbox, where every attachment, and link is inspected by FortiSandbox for malware before the email is forwarded to the user.
Out of Band Router
These are two old Cisco 2811 routers, attached to my Lab Environment on the same VLAN as my laptop. One unit has a Cisco Catalyst 16-port switch installed in it’s NME slot, which acts as a full Catalyst 3750 Layer-3 Switch. I use this to provide different WAN subnets at times to the SiteA-SiteE FortiGates if I want to show a feature and not have the WAN ports “neighbours” on the same VLAN. The second 2811 router has an NM-32-A reverse telnet Console Terminal Server running on it, that I use to access the Console Ports on multiple devices remotely without having to swap a console cable from appliance to appliance while writing a blog post. I just open multiple SSH sessions to the Cisco, and using a special port number, am connected in that session to the console on of the FortiGates or switches or other gear in the environment.